Configure GPG to sign Git commits (in Windows)
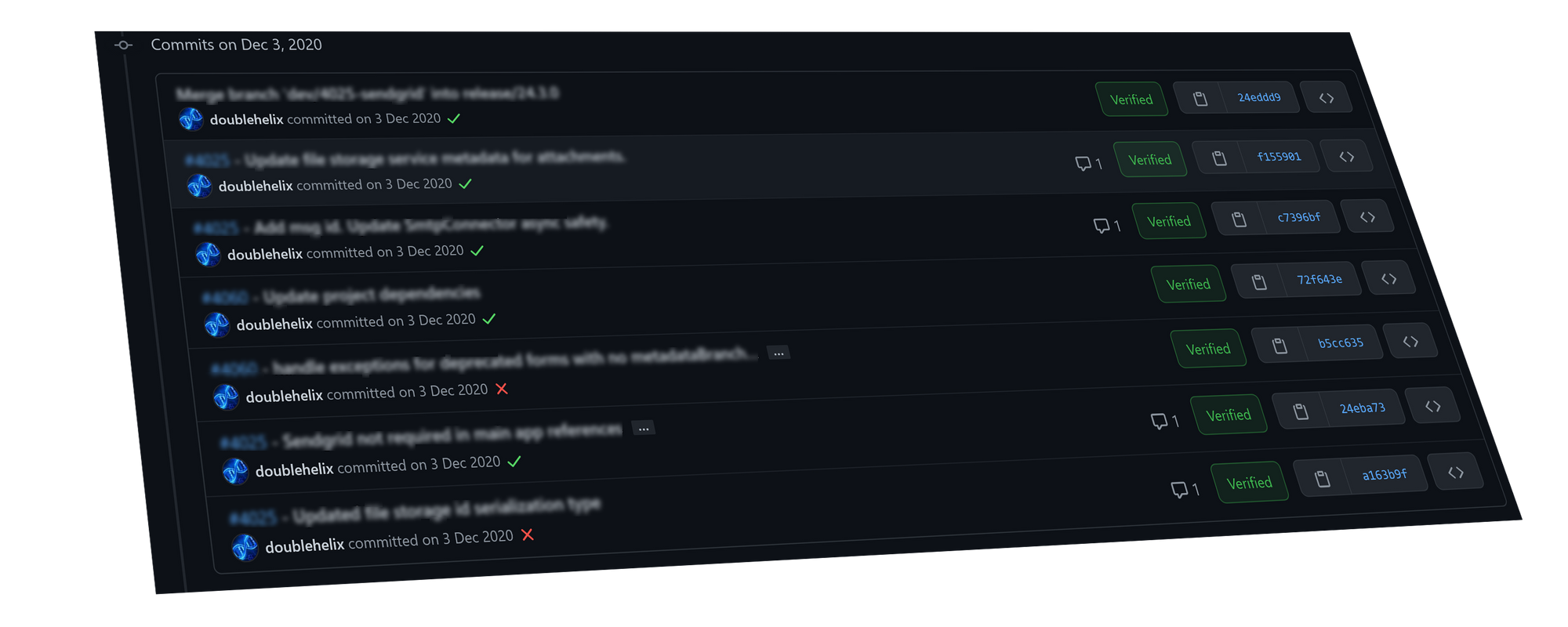
Configuring GPG to sign Git commits isn't trivial, especially if you need integration with an IDE such as VSCode or SourceTree.
Fortunately there's a straight forward set of steps you can take.
Install required software
You can skip any steps you've already completed, but in general you'll need to install the following:
- Git - https://git-scm.com/download/win
- GnuPG (GPG4Win) - https://gpg4win.org/download.html
Generate a new key
If you already have a PGP/GPG key you'd like to use, you can skip this step, if not follow the instructions here about generating a new GPG Key:
Backup, backup and re-backup
For most use cases, the secret key need not be exported and should not distributed. In order to create a backup key, use the export-backup option:
$ gpg --output backupkeys.pgp --armor --export-secret-keys --export-options export-backup [email protected] This will export all necessary information to restore the secrets keys including the trust database information. Make sure you store your backup secret keys in a secure physical location.
If this key is important to you, I recommend printing out the key on paper using paperkey, then optionally laminate it, and place the paper key in a fireproof/waterproof safe.
Export your public key
To export your public key, you'll first need to figure out your keys ID:gpg --list-secure-keys --key-id-format LONG
$ gpg --list-secret-keys --key-id-format LONG
# /c/Users/jsmith/.gnupg/secring.gpg
# ----------------------------------
# sec rsa4096/DA03396D49F620F3 2021-02-11 [SC] [expires: 2023-02-11]
# 802DB710FC9A7C5E4D9A6FA7DA03396D49F620F3
# uid [ultimate] Jane Smith <[email protected]>
Although you can use the full Thumbprint of the key (802DB710FC9A7C5E4D9A6FA7DA03396D49F620F3) you can also simply use the shorter Key ID (DA03396D49F620F3).
Next you'll need to dump the public key:
$ gpg --armor --export DA03396D49F620F3
# Prints the GPG key ID, in ASCII armor format, e.g.:
-----BEGIN PGP PUBLIC KEY BLOCK-----
mQINBGAk90sBEADC3l4nHixxcQ7XDbfWPs799uS92H25Z5g6SOJT6grqi+jRz425
gw4WBuZtRTrwz0zglpXkaVuCZMQT1vMrzxUbK1t/nv+SQyh0URr+wYFFCJcvpoce
dS00bQ9urOwaqXnIRuH2JnMUbTPPhp3BQJdrOFp46Itc1bURFd1ZRqoLgD/OItuu
nxP8Ncekdy1BdJJM94Mag+wEYoPfa8Q3qSeYU7zMr62KW+TGN8zNkBjEgWbq9nRT
dvm0GoqgVyBgWwffbPEgNHnFuDaCPWvkQ3bUr6vpGQewG2J8TsHYtRnOP5pkuX7A
wLcMq8zzKg79b53jpXHCVmdr91QsH5z4Ah630fjZTprFtfWzQrwolvRlH4v92vx7
PRRttasuQrjNjXY6BN9T4pQyKiepBMdTKhElLHVTZiiELxhoDBvRLznTqEelBflM
ZagoQLbXTE1F6C+l6/S8SCp1qJlBym6fVQG1tn91rxcC+RJqC99TBRYeL5xiNfp9
foZ4I0b8dg0UzsxC5cIHLxYThE3BKPR9y42BrLcG3zAxBrE3APWVJWPPN3epmaCZ
BIZMagCi4NaV6yxmT86Q37ByKiKm7Q+C1eYivGHHY/n01rvAr5NFkFVMbCBLyjaK
9ORaK9wFIMAcAvD6G3ls+yG+wMO6HKd1zWVR9GOGwCFRPAKv6XO78PZsSQARAQAB
tCBKYW1lcyBQcmljZSA8anByaWNlMjFAZ21haWwuY29tPokCVAQTAQgAPhYhBIAt
txD8mnxeTZpvp9oDOW1J9iDzBQJgJPdLAhsDBQkDwmcABQsJCAcCBhUKCQgLAgQW
AgMBAh4BAheAAAoJENoDOW1J9iDz7jQP/itHQ/Lg0t0fh9GkoV9YB2gR/Ap7tDUo
Bzt9loP+qCBHT00oo/fCDYxC3qJBpvjm7A0WpRzNEvWmwnEKAZMIRrDKVY2dU/Pq
tXuwhubvCwE0hFAnkIE88tZnbmRDYcwc9o2cqEYqakDjpupKZB2FhnV2qs8+yip6
1p2vJPi+ZtDUp8H12iqvfEBgLPAUi3NLyn2vk/koi7o4ir3Pd7o7MALaCujK6XO1
brEXVSeINGojejms+nXvbGFti/tYY1xVDmbOyA/CoJ+/Zx5Bu5yVlzpJJIZEaMwW
+GGrXS4ldZziP6F5VbKBapvDWuocK0m6qGUhVr76NND6BDJHWb4DdIYc59XEr2Pg
lJHcl1WBIR+xrtuzrKmJ+O2Fliq9NqSpT3UY7SwtZk6FEV6abbkIsFl1S8IGabf+
nMLbFce0TQ7qIjcfJEE7YyXWSNs1pHRPGNGMb+DGlhwvZZzLMu/XEoeNMErhXn1C
0EcNld2gyI9fjqlZw+GMFANFoRrhtIqs7b8jSunZs67s+SAah9IJMxiZMCMBh342
xskXrlKJvfcyosUBWZVlyRn149YsPbAAxPqGTLVFd1F/KaG2Bw6p8wZCXt+4jCSp
3fTa3q9PLswGsyT4XxWEdUVURMiT0qKW2J0DzXOYWr9EBwcayQBaALlMRNJe8+oT
vec6OdfFMLDh
=+nnP
-----END PGP PUBLIC KEY BLOCK-----
Copy this whole output (including the -----BEGIN PGP PUBLIC KEY BLOCK----- and -----END PGP PUBLIC KEY BLOCK-----, and everything in between). This is your public key... You need to register this key with GitHub.
Register you keys with GitHub
Open https://github.com/settings/keys
then click "New GPG key", paste your public key and click "Add GPG key"
(full instructions how to add GPG keys to GitHub in the link below):
Tell git to sign your commits!
This next command will instruct git to automatically sign all commits. It modified your global .gitconfig file. If you'd like to automatically sign commits to only the current repository, simply remove the --global from the commands below.
$ git config --global user.signingkey DA03396D49F620F3
$ git config --global commit.gpgsign trueThen, you have to tell git which GPG program you want it to use:
$ git config --global gpg.program "/c/Program Files (x86)/GnuPG/bin/gpg.exe"Optionally, you may need to disable TTY if your IDE doesn't like talking to gpg properly:
$ echo 'no-tty' >> ~/.gnupg/gpg.confIf you're using SourceTree, ensure that it's set to use the system git (that you just installed)
Are we done yet?
If everything's configured properly, the next time you commit anything in your git IDE, you should be asked to provide the password for th eGPG key you're signing with:
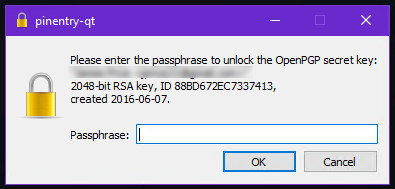
If you do, you're done. If not, have a look through the references below. You might be doing something different to me, or require extra steps for your IDE or version of git / gpg.
References
If you're using SourceTree on a Mac, you don't need to go to these lengths at all. See:
